Articles from: 2017
Securing Your Site and User Trust With SSL
Secure Sockets Layer (SSL) has two important functions associated with site security and integrity:
• When your SSL certificate is digitally signed by a trusted third party certificate authority, it helps to verify that your site is identifying itself correctly
• SSL encrypts all communications between the user and your site, making it difficult for somebody to extract anything useful even if they are able to intercept the communication
Every site that is owned by a business, non-profit organization, or government agency should have an SSL certificate. The only exception is where your site does not collect or disseminate any sensitive information.
When you have an SSL certificate, users can connect to your site via the HTTPS protocol. The “S” in HTTPS stands for “secure”. Although we use the term “SSL”, which is the one most people are familiar with, the standard has actually been superseded by something called TLS (Transport Layer Security). But you don’t need to worry about this because TLS is going to be enabled by default on any modern web server.
Even though the technology is enabled by default, sites that have an SSL certificate still need to set the HTTPS version of their site as the default protocol for inbound connections. A 2014 survey by Moz showed that less than 18% of respondents were already using HTTPS, and as recently as 2015, it was found that less than 2% of the top 1,000,000 sites had HTTPS set as the default protocol.
As a user, you can ensure that HTTPS is used whenever possible regardless of a site’s default settings by installing the HTTPS Everywhere plug-in.
SEO advantages
Using SSL may give your site a boost in Google rankings. In August 2014, Google announced that it would take SSL into account as a ranking factor.
It also must be considered that HTTPS does slightly lower the speed of a site, so if your site is already slow (which it shouldn’t be – fix it!), you could see your rank actually slip as a result of adding HTTPS. It will really come down to the differential between the benefit from HTTPS and the benefit from having a fast site.
Google wants sites to use HTTPS because it makes it easier to verify the integrity of a site, but that doesn’t automatically mean you need to do it. Most sites will benefit from having HTTPS, but because SSL certificates aren’t free, you might choose not to have one if the cost can’t be justified.
Risk vs. reward: the privacy and security advantages of SSL
You have to think about the financial cost of purchasing and renewing your SSL certificate. If there’s nothing on your site that needs to be confidential, you may not need to go to the trouble.
But if your site collects personal information from the user, has password authenticated log-ins, or engages in any sort of e-Commerce, you absolutely must have SSL if you want to avoid problems and retain the full confidence and trust of your users.
How to get an SSL certificate
Buying an SSL certificate is not like a regular purchase, because there are a few tests and checks that have to be done before a certificate can be issued. This is for the protection of everyone, including you. Usually the easiest way is to get your Hosting company or SEO manager to obtain the certificate for you, because this will simplify the process greatly.
If you’d prefer to do it entirely on your own, your first step is to generate a Certificate Signing Request (CSR) on your server. This is a block of encrypted text that looks similar to a PGP signature. What you need to type to generate the request depends on what server software your web host is running.
Most websites are hosted on Apache servers, and Apache uses a service called OpenSSL to generate a CSR. Here’s an example of how to generate a CSR for a company called Widgets-R-Us Inc, with domain widgets.com, based in Los Angeles:
openssl req -new -newkey rsa:2048 -nodes -out widgets_com.csr -keyout widgets_com.key -subj “C/=US/ST=California/L=Los Angeles/O=Widgets R Us Inc./CN=widgets.com”
The section that’s relevant about the company is the -subj section. This contains a string value with specific values, as follows:
• C is a 2 digit country code, for example: US, UK, IE, FR, DE, BE, and so on.
• ST is the state or province
• L is the city
• O is the organization name
• CN is the “common name”, which is a fully qualified domain name (FQDN).
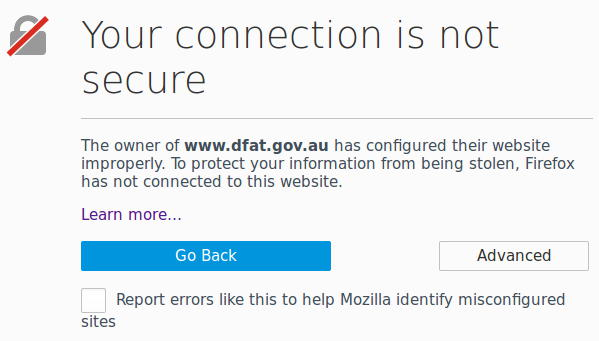
There’s an optional value called OU that can appear between O and CN, but it is rarely used, and can cause problems. Currently (at the time of writing) the SSL certificate of Australia’s Department of Foreign Affairs and Trade is affected, for example. OU stands for “organizational unit” and means a department within the organisation.
After generating the CSR, it would look something like:
—–BEGIN CERTIFICATE REQUEST—– MIIHVjCCBj6gAwIBAgIQVXENtd02KRwAAAAAUNuvdTANBgkqhkiG9w0BAQsFADCB ujELMAkGA1UEBhMCVVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xKDAmBgNVBAsT H1NlZSB3d3cuZW50cnVzdC5uZXQvbGVnYWwtdGVybXMxOTA3BgNVBAsTMChjKSAy MDEyIEVudHJ1c3QsIEluYy4gLSBmb3IgYXV0aG9yaXplZCB1c2Ugb25seTEuMCwG A1UEAxMlRW50cnVzdCBDZXJ0aWZpY2F0aW9uIEF1dGhvcml0eSAtIEwxSzAeFw0x NzAzMDIyMjA5MzNaFw0xODAzMDIyMjM5MzFaMIGNMQswCQYDVQQGEwJBVTElMCMG
—–END CERTIFICATE REQUEST—–
In this case it is contained in the generated file “widgets_com.csr”. You need to open that file in a text editor, then cut and paste all the text (including the begin and end instructions) into the online form of the SSL certificate authority you are ordering from. Do not confuse the csr file with the key file.
Once the certificate authority has validated your domain and company, it will email you a copy of your SSL certificate, which you then need to install on your server.
Due to the complexity involved, most people prefer to have professional assistance rather than opting to do it themselves.
Do Cloud-Based Email Solutions Offer an Advantage?
Cloud services are all the rage at the moment, but it’s not necessarily true that every cloud has a silver lining. When choosing which services are right for your business, you need to consider all the pros and cons of the different options available. And while some services are being heavily hyped and marketed as the way forward, it must be remembered that all marketing has an agenda, and that agenda does not necessarily fit hand in hand with your own.
What is necessary is to strip away all the bias and hype, and look carefully at each factor which would affect your decision. Only in this way can an objective view be created. That’s the purpose of this article, and hopefully by the end of it we’ll have an answer to the title question.
1. Access and Storage
These two items need to be considered together at the same time because they’re linked too closely for it to be worth separating them. When your email communications are hosted traditionally, messages take up space on your web server until they’re downloaded or deleted.
Once messages are downloaded, they are only available from the place they are downloaded to, and any devices that are able to access that location. With a cloud-based solution, the messages are stored on a 3rd party server, and there’s no need for you to worry about how much space they are taking up unless you’re close to the limit offered by the provider.
Advantages:
• Messages won’t affect the performance, storage quota, or bandwidth quota of your website
• Messages won’t normally take up space on your own devices, except temporarily
• Cloud-based solutions often have great management and curation features
• May make it easier to share emails among work teams
• May (sometimes) protect against malicious payloads
• Can be accessed from anywhere that you can connect to the Internet
Disadvantages:
• Messages can only be viewed if you have a working Internet connection
• Many cloud-based services do not allow messages to be downloaded
• You can’t be certain whether deleted messages are really deleted
• Most free (and some paid) services discourage or disallow encryption
• Can be very difficult to obtain and preserve true anonymity with cloud-based services
• You may need to frequently delete messages if you have a storage limit
• International travel can be a problem, as some services may deny you access when you log in from another country.
2. Security
Depending on the nature of your business, this could be a major concern for you. It can be especially important for people dealing with matters related to national security, law enforcement, crime, health services, and financial services. Some of the key points were already mentioned in the previous section.
Advantages:
• No known privacy or security advantages. You are trusting a 3rd party with your confidential information, with absolutely no control over how that 3rd party might access or use that information. Even if you trust an organization to do the right thing, you may not know if you can trust each individual employee, because even the organization does not know if they can be trusted.
Disadvantages:
• No control over the storage, copying, and archiving of your messages
• Encryption may not be supported, and in some cases may be against the terms and conditions
• Messages are stored online, not locally, so if the provider is hacked, you could be compromised
• When messages are stored online, vulnerability from staff being socially engineered is increased
• Many services provide unwanted protections that may cause more problems than they solve
• Almost every cloud-based service states they will release your information to government officials if asked (not ordered by a court, just asked). There are a few exceptions to this. Most of them also say they will not inform you if they do hand over your information to government officials.
3. Preservation
In general, cloud-based services offer better preservation of your communications compared with traditional hosting where messages are downloaded to a local device.
Advantages:
• Messages are often stored indefinitely and may be automatically backed up to multiple locations.
• You are protected from data loss due to local device hardware malfunction
Disadvantages:
• No certainty that deleted messages will be deleted
• Losing your password may deny you access to your own account
• Service provider may decide to deny access to you at any time and for any reason
4. Management
With traditional hosting, you are free to define whatever email management policies you like. When you use cloud-based services, the provider may impose their own policies over the top of yours, or at least in addition to yours.
Advantages:
• May help reduce the amount of spam you receive
• May provide more advanced management options than your regular email software provides
Disadvantages:
• Messages may be incorrectly flagged as spam, often for ridiculous reasons
• Messages may be denied from certain senders just because of the IP address their host uses
• When messages are denied, you may not even be aware that it has happened
5. Support
In general, most cloud-based services do provide good support (though some provide almost no support). Ordinary hosting doesn’t usually provide great email support unless you have a problem of a technical nature. The quality of the support you receive depends entirely on what the service provider is prepared to offer, and the combined skills and experience of the support staff in dealing with technical problems.
Advantages:
• Some cloud-based email services have excellent support available
• Support is usually available 24/7
Disadvantages:
• Many services outsource their support (normally negative)
• Support staff may not have proper technical training and solutions may be prepared from scripts
Conclusions
While there are many positive aspects to cloud-based email services, there seems to be more negatives. The biggest problem is in the matter of security, because messages are stored online indefinitely, and normally in plain text (unencrypted), so if the provider is compromised, then so are you. There is also the possibility of employees of the provider to read the communications, either due to boredom or with criminal intent.
For these reasons, the majority of businesses would actually be better off not using cloud-based email services and sticking with traditional hosting for email services, downloading their communications to local devices, and following a sensible backup and security plan. The convenience of being able to access your communications from anywhere on any device is also a vulnerability.
Plus of course, any important internal communications should be properly encrypted (there is no good reason not to do this), and that’s not always possible with cloud-based services.
Why G Suite Could Be For You!
Last year Google rebranded their business apps to G Suite. This quick video may help you decide if this Google product is worth exploring further!